HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 169
Admin Domain interaction with Fabric OS features
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 169 highlights
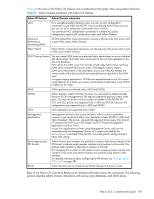
Table 49 lists some of the Fabric OS features and considerations that apply when using Admin Domains. Table 49 Admin Domain interaction with Fabric OS features Fabric OS feature Admin Domain interaction ACLs Advanced Performance Monitoring (APM) Fabric Watch If no user-defined Admin Domains exist, you can run ACL configuration commands in only AD0 and AD255. If any user-defined Admin Domains exist, you can run ACL configuration commands only in AD255. You cannot use ACL configuration commands or validate ACL policy configurations against AD membership under each Admin Domain. All APM-related filter setup and statistics viewing is allowed only if the local switch is part of the current Admin Domain. Fabric Watch configuration operations are allowed only if the local switch is part of the current Admin Domain. FC-FC Routing Service You can create LSAN zones as a physical fabric administrator or as an individual AD administrator. The LSAN zone can be part of the root zone database or the AD zone database. FCR collects the LSAN zones from all ADs. If both edge fabrics have matching LSAN zones and both devices are online, FCR triggers a device import. LSAN zone enforcement in the local fabric occurs only if the AD member list contains both of the devices (local and imported device) specified in the LSAN zone. To support legacy applications, WWNs are reported based on the AD context using NAA=5. As a result, you cannot use the NAA=5 field alone in the WWN to detect an FC router. FDMI FDMI operations are allowed only in AD0 and AD255. FICON Admin Domains support FICON. However, you must perform additional steps because FICON management (CUP) requires additional physical control of the ports. You must set up the switch as a physical member of the FICON AD. DCC and SCC policies are supported only in AD0 and AD255, because ACL configurations are supported only in AD0 and AD255. iSCSI iSCSI operations are supported only in AD0. Management applications Management interfaces that access the fabric without a user's credentials continue to get the physical fabric view. Examples include: SNMPV1, Web Tools, Fabric Manager; http access, unzoned Management Server query, FAL in-band CT requests from FAL Proxy to FAL Target, and FC-CT based management applications (such as Tivoli). Access from applications or hosts using Management Server calls can be controlled using the Management Server ACL support provided by the msConfigure command. Note that this is a switch-specific setting and not a fabric-wide setting. Port-Swapping and PID formats RSCN Admin Domain port members are specified in domain,index format. Based on the PID format, a domain,index member indicates a slot and port in the switch. The domain,index member is effectively a member of that AD. Port swapping has no effect on AD support as port swapping swaps only the area numbers of two ports and Admin Domains are specified using domain,index members. For detailed information about configuring the PID format, see "Configuring the PID format" on page 381. Admin Domains do not introduce any RSCN changes to devices or hosts. Refer to the Fabric OS Command Reference for detailed information about the commands. The following sections describe Admin Domain interactions with zones, zone databases, and LSAN zones. Fabric OS 6.1.x administrator guide 169