HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 387
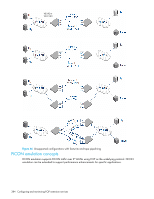
Configuring IPSec
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 387 highlights
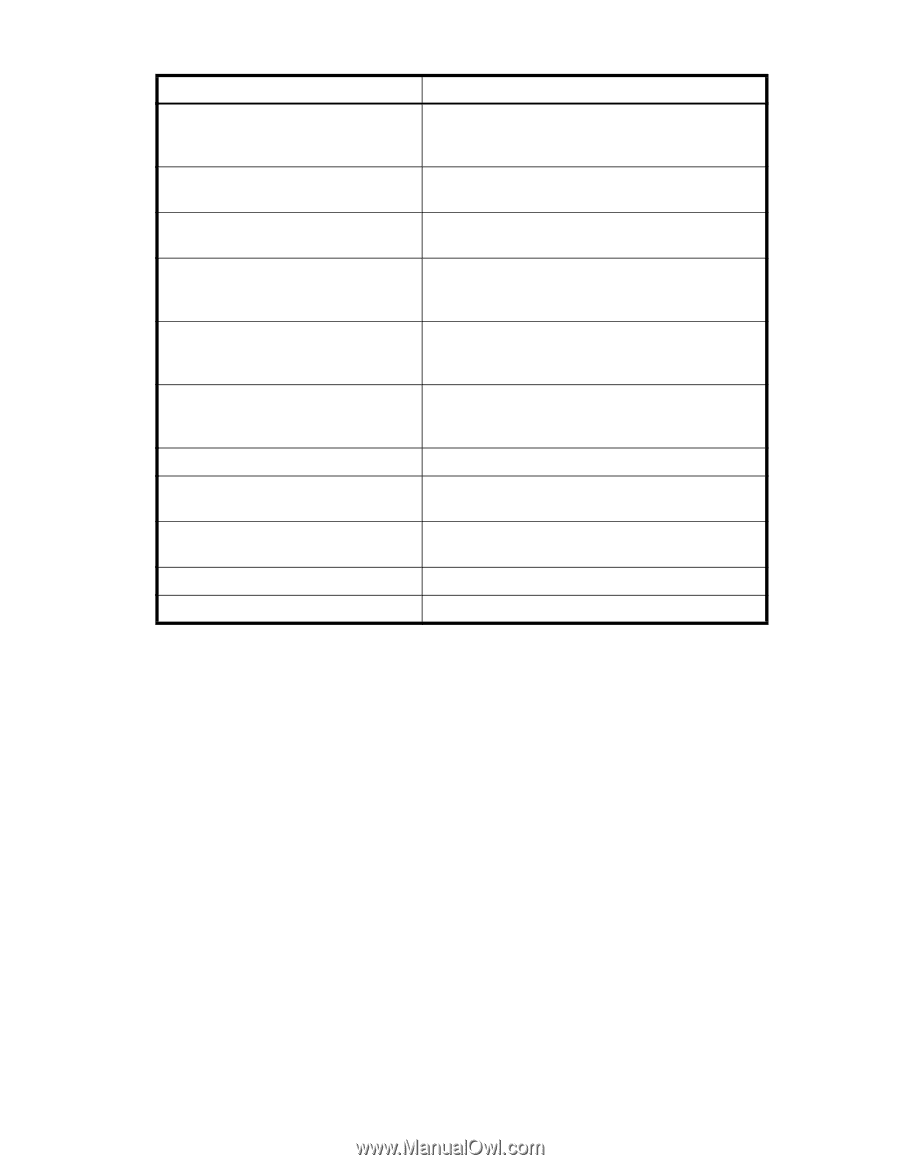
Table 89 Command checklist for configuring FCIP links (continued) Step Command 3. If a VEX port is to be implemented, portcfgvexport configure the appropriate virtual port as a VEX_Port. 4. Configure the IP interface for both ports of a tunnel. portcfg ipif 5. Verify the IP interface for both ports portshow ipif of a tunnel. 6.Create one or more IP routes portcfg iproute connecting the IP interfaces across the IP network. 7. Create ARP entry for the IP interface if portcfg arp add VLAN tagging is to be implemented. (For IPv4 only, not required for IPv6). 8.Test IP connectivity between the local Ethernet interface (ge0 or ge1) and a destination IP address. portcmd - -ping 9. Configure FCIP tunnels. 10. If you are implementing FICON emulation, configure FICON emulation. portcfg fciptunnel portcfg ficon 11. If you are implementing FTRACE, configure FTRACE. portcfg ftrace 12. Verify FCIP tunnels. 13. Enable the ports. portshow fciptunnel portpersistentenable Configuring IPSec IPSec requires predefined configurations for IKE and IPSec. You can enable IPSec only when these configurations are well-defined and properly created in advance. The following describes the sequence of events that invokes the IPSec protocol. 1. Traffic from an IPSec peer with the lower local IP address initiates the IKE negotiation process. 2. IKE negotiates SAs and authenticates IPSec peers, and sets up a secure channel for negotiation of phase 2 (IPSec) SAs. 3. IKE negotiates SA parameters, setting up matching SAs in the peers. Some of the negotiated SA parameters include encryption and authentication algorithms, Diffie-Hellman key exchange, and SA lifetimes. 4. Data is transferred between IPSec peers based on the IPSec parameters and keys stored in the SA database. 5. IPSec tunnel termination. SA lifetimes terminate through deletion or by timing out. All of these steps require that the correct policies have been created. Because policy creation is an independent procedure from FCIP tunnel creation, you must know which IPSec configurations have been created. This ensures that you choose the correct configurations when you enable an IPSec tunnel. The first step to configuring IPSec is to create a policy for IKE and a policy for IPSec. Once the policies have been created, you assign the policies when creating the FCIP tunnel. IKE negotiates SA parameters and authenticates the peer using the preshared key authentication method. Once the 2 phases of the negotiation are completed successfully, the actual encrypted data transfer can begin. Fabric OS 6.1.x administrator guide 387