HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 380
IKE stands for Internet Key Exchange. IKE is defined in RFC 2407, RFC 2408
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 380 highlights
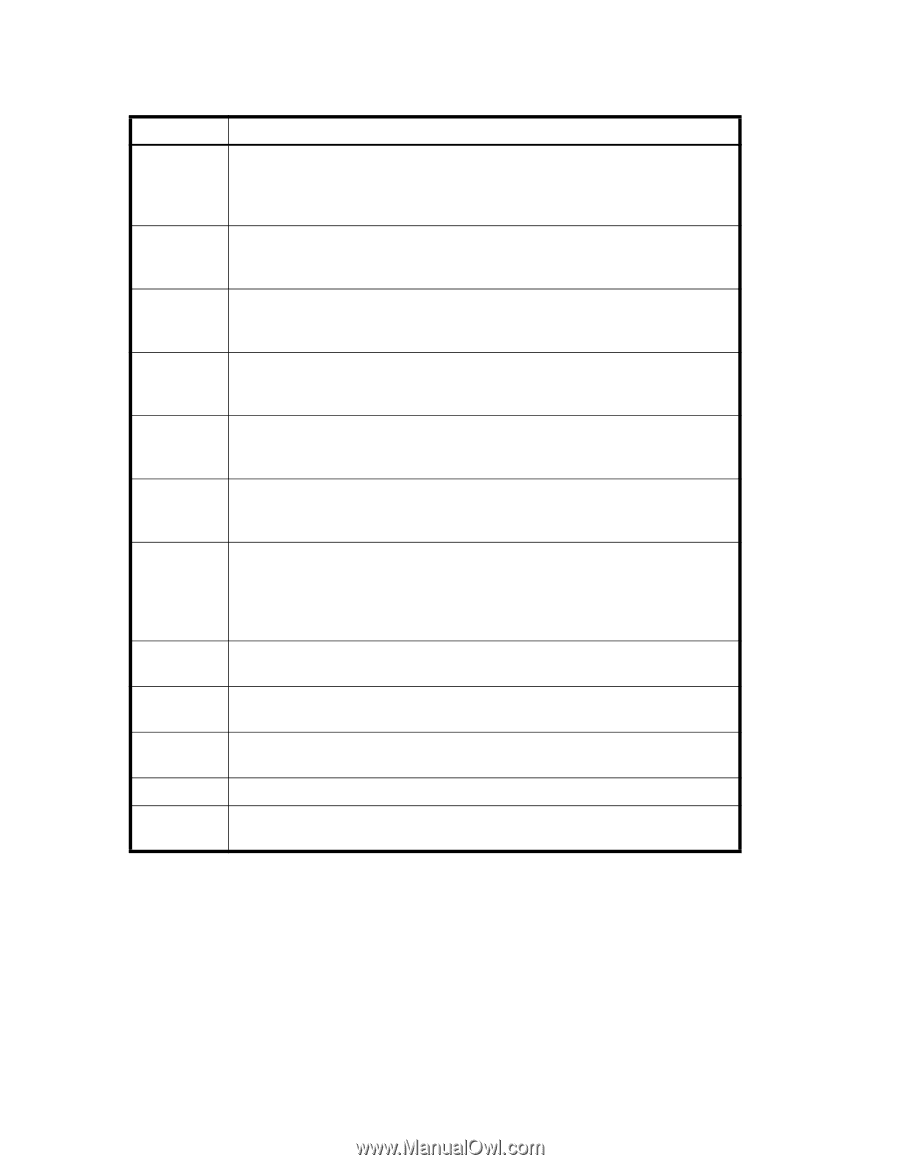
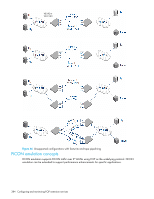
IPSec uses some terms that you should be familiar with before beginning your configuration. These are standardized terms, but are included here for your convenience. Table 87 IPSec terminology Term AES AES-XCBC AH DES 3DES ESP IKE MD5 SHA MAC HMAC SA Definition Advanced Encryption Standard. FIPS 197 endorses the Rijndael encryption algorithm as the approved AES for use by US Government organizations and others to protect sensitive information. It replaces DES as the encryption standard. Cipher Block Chaining. A key-dependent one-way hash function (MAC) used with AES in conjunction with the Cipher-Block-Chaining mode of operation, suitable for securing messages of varying lengths, such as IP datagrams. Authentication Header - like ESP, AH provides data integrity, data source authentication, and protection against replay attacks but does not provide confidentiality. Data Encryption Standard is the older encryption algorithm that uses a 56-bit key to encrypt blocks of 64-bit plain text. Because of the relatively shorter key length, it is not a secured algorithm and no longer approved for Federal use. Triple DES is a more secure variant of DES. It uses three different 56-bit keys to encrypt blocks of 64-bit plain text. The algorithm is FIPS-approved for use by Federal agencies. Encapsulating Security Payload is the IPSec protocol that provides confidentiality, data integrity and data source authentication of IP packets, and protection against replay attacks. IKE stands for Internet Key Exchange. IKE is defined in RFC 2407, RFC 2408 and RFC 2409. IKEv2 is defined in RFC 4306. IKE uses a Diffie-Hellman key exchange to set up a shared session secret, from which cryptographic keys are derived, and communicating parties are authenticated. The IKE protocol creates a security association (SA) for both parties. Message Digest 5, like SHA-1, is a popular one-way hash function used for authentication and data integrity. Secure Hash Algorithm, like MD5, is a popular one-way hash function used for authentication and data integrity. Message Authentication Code is a key-dependent, one-way hash function used for generating and verifying authentication data. A stronger MAC because it is a keyed hash inside a keyed hash. Security Association is the collection of security parameters and authenticated keys that are negotiated between IPSec peers. The following limitations apply to using IPSec: • IPv6, NAT, and AH are not supported. • You can only create a single secure tunnel on a port; you cannot create a nonsecure tunnel on the same port as a secure tunnel. • IPSec-specific statistics are not supported. • To change the configuration of a secure tunnel, you must delete the tunnel and recreate it. • Jumbo frames are not supported for IPSec. • There is no RAS message support for IPSec. • Only a single route is supported on an interface with a secure tunnel. 380 Configuring and monitoring FCIP extension services