HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 88
The SSH protocol
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
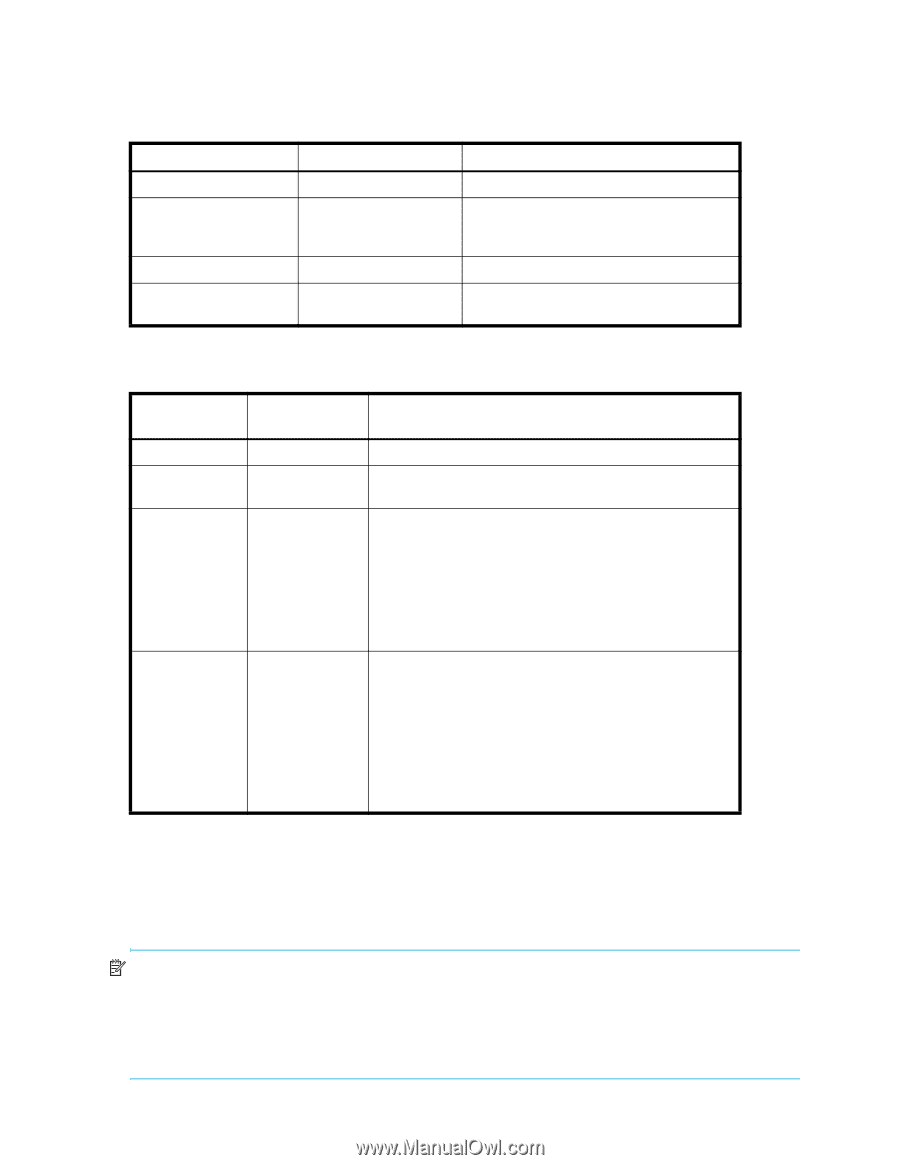
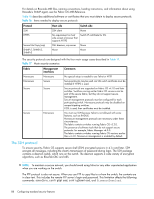
For details on Brocade MIB files, naming conventions, loading instructions, and information about using Brocade's SNMP agent, see the Fabric OS MIB Reference. Table 16 describes additional software or certificates that you must obtain to deploy secure protocols. Table 16 Items needed to deploy secure protocols Protocol Host side Switch side SSH SSH client None HTTPS No requirement on host side except a browser that supports HTTPS Switch IP certificate for SSL Secure File Copy (scp) SSH daemon, scp server None SNMPv1, SNMPv2, SNMPv3 None None The security protocols are designed with the four main usage cases described in Table 17. Table 17 Main security scenarios Fabric Nonsecure Nonsecure Secure Secure Management interfaces Nonsecure Secure Secure Nonsecure Comments No special setup is needed to use Telnet or HTTP. Secure protocols may be used. An SSL switch certificate must be installed if HTTPS is used. Secure protocols are supported on Fabric OS v4.1.0 and later switches. Switches running earlier Fabric OS versions can be part of the secure fabric, but they do not support secure management. Secure management protocols must be configured for each participating switch. Nonsecure protocols may be disabled on nonparticipating switches. If SSL is used, then certificates must be installed. You must use SSH because Telnet is not allowed with some features, such as RADIUS. Nonsecure management protocols are necessary under these circumstances: The fabric contains switches running Fabric OS v3.2.0. The presence of software tools that do not support secure protocols: for example, Fabric Manager v4.0.0. The fabric contains switches running Fabric OS versions earlier than v4.4.0. Nonsecure management is enabled by default. The SSH protocol To ensure security, Fabric OS supports secure shell (SSH) encrypted sessions in 4.1.x and later. SSH encrypts all messages, including the client's transmission of password during login. The SSH package contains a daemon (sshd), which runs on the switch. The daemon supports a wide variety of encryption algorithms, such as Blowfish-CBC and AES. NOTE: To maintain a secure network, you should avoid using Telnet or any other unprotected application when you are working on the switch. The FTP protocol is also not secure. When you use FTP to copy files to or from the switch, the contents are in clear text. This includes the remote FTP server's login and password. This limitation affects the following commands: saveCore, configUpload, configDownload, and firmwareDownload. 88 Configuring standard security features