HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.1.x administrator guide (5697 - Page 136
Power-up self tests, Conditional tests, FIPS mode
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 136 highlights
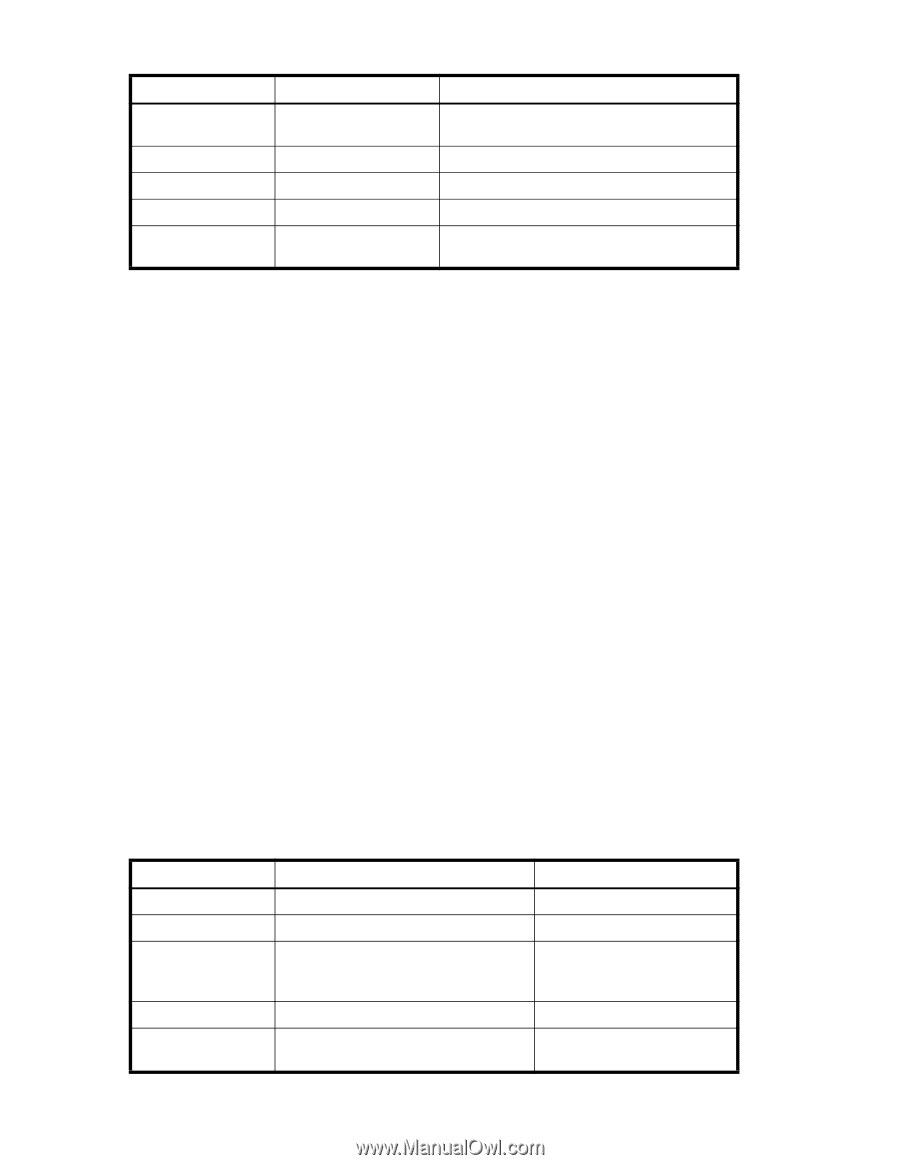
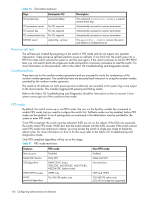
Table 40 Zeroization behavior Keys Zeroization CLI TLS private keys seccertutil delkey TLS pre-master secret TLS session key TLS authentication key RADIUS secret No CLI required No CLI required No CLI required aaaconfig --remove Description The command seccertutil delkey is used to zeroize these keys. Automatically zeroized on session termination Automatically zeroized on session termination Automatically zeroized on session termination The aaaconfig --remove zeroizes the secret and deletes a configured server Power-up self tests The self tests are invoked by powering on the switch in FIPS mode and do not require any operator intervention. These power-up self tests perform power-on self-tests. If any KATs fail, the switch goes into a FIPS Error state which reboots the system to start the tests again. If the switch continues to fail the FIPS POST tests, you will need to boot into single-user mode and perform a recovery procedure to reset the switch. For more information on this procedure, refer to the Fabric OS Troubleshooting and Diagnostics Guide. Conditional tests These tests are for the random number generators and are executed to verify the randomness of the random number generator. The conditional tests are executed each time prior to using the random number provided by the random number generator. The results of all self-tests, for both power-up and conditional, are recorded in the system log or are output to the local console. This includes logging both passing and failing results. Refer to the Fabric OS Troubleshooting and Diagnostics Guide for instructions on how to recover if your system cannot get out of the conditional test mode. FIPS mode By default, the switch comes up in non-FIPS mode. You can run the fipsCfg --enable fips command to enable FIPS mode, but you need to confgure the switch first. Self-tests mode must be enabled, before FIPS mode can be enabled. A set of prerequisites as mentioned in the table below must be satisfied for the system to enter FIPS mode. To be FIPS-compliant, the switch must be rebooted. KATs are run on the reboot. If the KATs are successful, the switch enters FIPS mode. If KATs fail, then the switch reboots until the KATs succeed. If the switch cannot enter FIPS mode and continues to reboot, you must access the switch in single-user mode to break the reboot cycle. For more information on how to fix this issue, refer to the Fabric OS Troubleshooting and Diagnostics Guide. Only FIPS compliant algorithms will be run at this stage. Table 41 FIPS mode restrictions Features FIPS mode Non-FIPS mode Root account Telnet/SSH access SSH algorithms HTTP/HTTPS access HTTPS protocol/algorithms Disabled Only SSH HMAC-SHA1 (mac) 3DES-CBC, AES128-CBC, AES192-CBC, AES256-CBC (cipher suites) HTTPS only TLS/AES128 cipher suite Enabled Telnet and SSH No restrictions HTTP and HTTPS TLS/AES128 cipher suite (SSL will no longer be supported) 136 Configuring advanced security features