HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 148
Securing the management interface
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 148 highlights
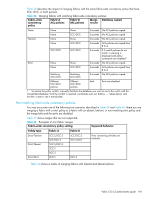
Table 40 Fabric merges with tolerant/absent combinations Fabric-wide consistency policy setting Expected behavior Policy type Fabric A Fabric B Tolerant/Absent SCC;DCC DCC SCC;DCC SCC DCC SCC Error message logged. Run fddCfg --fabwideset "" from any switch with the desired configuration to fix the conflict. The secPolicyActivate command is blocked until conflict is resolved. Securing the management interface You can secure an Ethernet management interface between two B-Series switches or enterprise-class platforms by implementing IPsec and IKE policies to create a tunnel that protects traffic flows. The tunnel has at each end a B-Series switch or enterprise-class platform. There may be routers, gateways, and firewalls in between the two ends. IMPORTANT: Enabling secure IPsec tunnels does not provide IPsec protection for traffic flows on the external management interfaces of intelligent blades in a chassis, nor does it support protection of traffic flows on FCIP interfaces. Internet Protocol security (IPsec) is a framework of open standards that ensures private and secure communications over Internet Protocol (IP) networks through the use of cryptographic security services. The goal of IPsec is to provide the following capabilities: • Authentication: Ensures that the sending and receiving end-users and devices are known and trusted by one another. • Data Integrity: Confirms that the data received was in fact the data transmitted. • Data Confidentiality: Protects the user data being transmitted, such as utilizing encryption to avoid sending data in clear text. • Replay Protection: Prevents replay attack, a type of denial of service (DoS) attack where an attacker intercepts a series of packets and resends them to cause the recipient to waste CPU cycles processing them. • Automated Key Management: Automates the process, as well as manages the periodic exchange and generation of new keys. Using the ipsecConfig command, you must configure multiple security policies for traffic flows on the Ethernet management interfaces based on IPv4 or IPv6 addresses, a range of IPv4 or IPv6 addresses, the type of an application, port numbers, and port types used (UDP/TCP). You must specify the transforms and processing choices for the traffic flow (drop, protect or bypass). Also, you must select and configure the key management protocol using an automatic or manual key. For more information on IPv4 and IPv6 addressing, see Chapter 1, "Performing basic configuration tasks" on page 29. Configuration examples This section contains several examples of various configurations you can use to implement an IPsec tunnel between two devices. Endpoint-to-Endpoint Transport or Tunnel In this scenario, both endpoints of the IP connection implement IPsec, as required of hosts in RFC4301. The transport mode is commonly used with no inner IP header. If there is an inner IP header, the inner addresses will be the same as the outer addresses. A single pair of addresses will be negotiated for packets protected by this SA (see Figure 5). 146 Configuring advanced security features