HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 151
Block ciphers, Blowfish
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 151 highlights
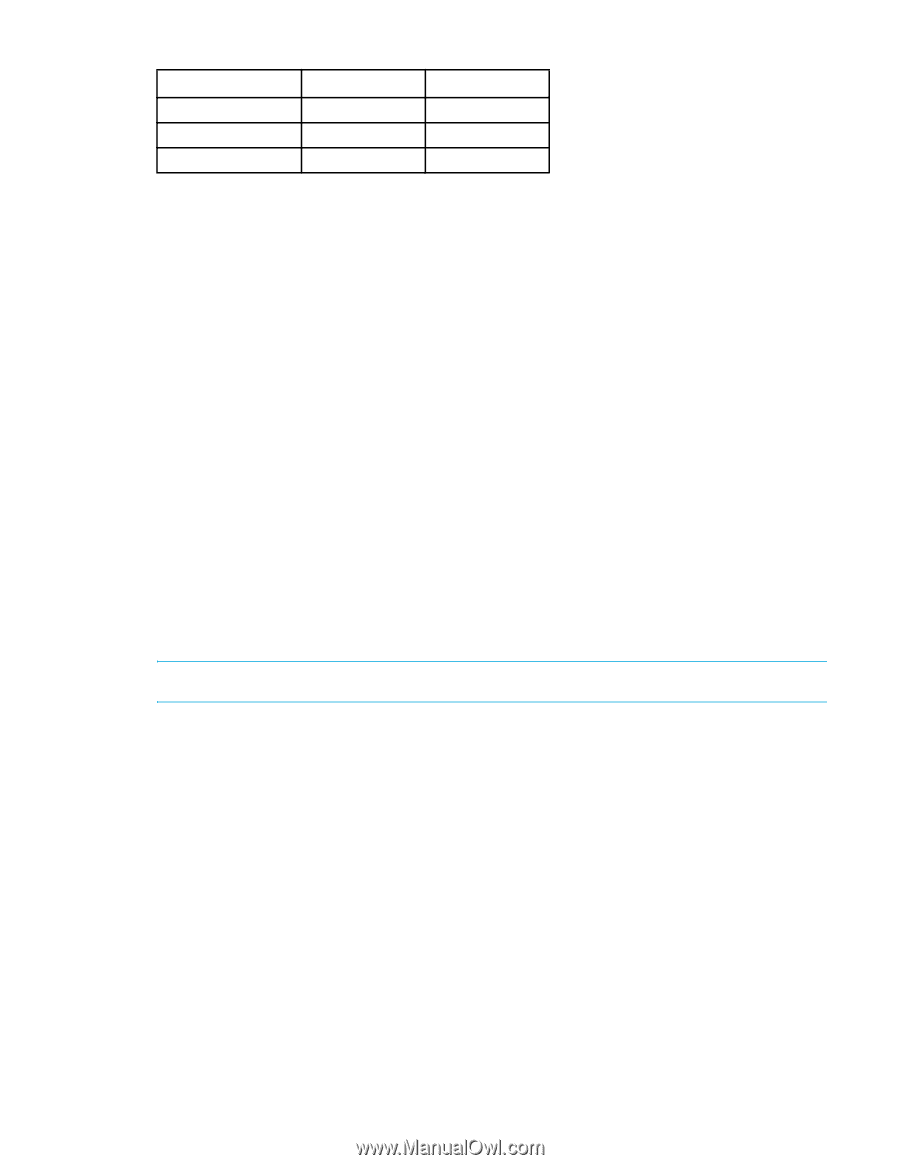
Table 41 Algorithms and associated authentication policies Algorithm Encryption Level Policy aes128_cbc 128-bit ESP aes256_cbc 256-bit ESP null_enc n/a ESP Block ciphers In cryptography, a block cipher is a symmetric key cipher which operates on fixed-length groups of bits, termed blocks, with an unvarying transformation. For example, when encrypting, a block cipher might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext. The exact transformation is controlled using a second input-the secret key. Decryption is similar: the decryption algorithm takes, in this example, a 128-bit block of ciphertext together with the secret key, and yields the original 128-bit block of plaintext. To encrypt messages longer than the block size (128 bits in the above example), a mode of operation is used. A mode of operation is a block cipher that operates on blocks of fixed length, often 64 or 128 bits. In the cipher-block chaining (CBC) mode, each block of plaintext is exclusive or'ed (XOR'ed) with the previous ciphertext block before being encrypted. This way, each ciphertext block is dependent on all plaintext blocks processed up to that point. HMAC A keyed-Hash Message Authentication Code (HMAC or KHMAC), is a type of message authentication code (MAC) calculated using a specific algorithm involving a cryptographic hash function in combination with a secret key. As with any MAC, it may be used to simultaneously verify that both the data integrity and the authenticity of a message. Any iterative cryptographic hash function, such as MD5 or SHA-1, may be used in the calculation of an HMAC; the resulting MAC algorithm is termed HMAC-MD5 or HMAC-SHA-1 accordingly. An iterative hash function breaks up a message into blocks of a fixed size and iterates over them with a compression function. For example, MD5 and SHA-1 operate on 512-bit blocks. The size of the output of HMAC is the same as that of the underlying hash function (128 or 160 bits in the case of MD5 or SHA-1, respectively), although it can be truncated if desired. NOTE: The MD5 hash algorithm is blocked when FIPS mode is enabled. 3DES Triple DES (3DES or TDES) is a block cipher formed from the Data Encryption Standard (DES) cipher by using it three times. The DES is a public standard, published by the National Institute of Standards and Technology, and is also known as the Data Encryption Algorithm (DEA). When it was found that a 56-bit key of DES is not enough to guard against brute force attacks, DES was chosen as a simple way to enlarge the key space without a need to switch to a new algorithm. The use of three steps is essential to prevent meet-in-the-middle attacks that are effective against double DES encryption. Note that DES is not a group; if it were, the TDES construction would be equivalent to a single DES operation and would be no more secure. Blowfish Blowfish is a keyed, symmetric block cipher that provides a good encryption rate in software. No effective cryptanalysis of it has been found to date. It takes a variable-length key, from 32-bits to 448-bits, making it ideal for both domestic and exportable use. Blowfish is one of the fastest block ciphers in widespread use, except when changing keys. Each new key requires pre-processing equivalent to encrypting about 4 kilobytes of text, which is very slow compared to other block ciphers. AES Advanced Encryption Standard (AES) is a block cipher that has a fixed block size of 128-bit and a key size of 128-, 192-, or 256-bit. AES is a substitution-permutation network (series of linked mathematical Fabric OS 6.2 administrator guide 149