HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 465
IPsec configuration
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 465 highlights
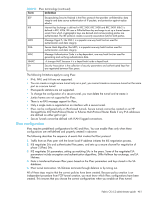
Table 92 IPsec terminology (continued) Term Definition ESP IKE MD5 Encapsulating Security Payload is the IPsec protocol that provides confidentiality, data integrity and data source authentication of IP packets, and protection against replay attacks. Internet Key Exchange is defined in RFC 2407, RFC 2408 and RFC 2409. IKEv2 is defined in RFC 4306. IKE uses a Diffie-Hellman key exchange to set up a shared session secret, from which cryptographic keys are derived and communicating parties are authenticated. The IKE protocol creates a security association (SA) for both parties. Message Digest 5, like SHA-1, is a popular one-way hash function used for authentication and data integrity. SHA MAC HMAC SA Secure Hash Algorithm, like MD5, is a popular one-way hash function used for authentication and data integrity. Message Authentication Code is a key-dependent, one-way hash function used for generating and verifying authentication data. A stronger MAC because it is a keyed hash inside a keyed hash. Security Association is the collection of security parameters and authenticated keys that are negotiated between IPsec peers. The following limitations apply to using IPsec: • IPv6, NAT, and AH are not supported. • You can create a single secure tunnel only on a port; you cannot create a nonsecure tunnel on the same port as a secure tunnel. • IPsec-specific statistics are not supported. • To change the configuration of a secure tunnel, you must delete the tunnel and re-create it. • Jumbo frames are not supported for IPsec. • There is no RAS message support for IPsec. • Only a single route is supported on an interface with a secure tunnel. • IPsec can be configured only on IPv4 based tunnels. Secure tunnels cannot be created on an HP StorageWorks 400 Multi-Protocol Router or B-Series Multi-Protocol Router Blade if any IPv6 addresses are defined on either ge0 or ge1. • Secure Tunnels cannot be defined with VLAN Tagged connections. IPsec configuration IPsec requires predefined configurations for IKE and IPsec. You can enable IPsec only when these configurations are well-defined and properly created in advance. The following describes the sequence of events that invokes the IPsec protocol. 1. Traffic from an IPsec peer with the lower local IP address initiates the IKE negotiation process. 2. IKE negotiates SAs and authenticates IPsec peers, and sets up a secure channel for negotiation of phase 2 (IPsec) SAs. 3. IKE negotiates SA parameters, setting up matching SAs in the peers. Some of the negotiated SA parameters include encryption and authentication algorithms, Diffie-Hellman key exchange, and SA lifetimes. 4. Data is transferred between IPsec peers based on the IPsec parameters and keys stored in the SA database. 5. IPsec tunnel termination. SA lifetimes terminate through deletion or by timing out. All of these steps require that the correct policies have been created. Because policy creation is an independent procedure from FCIP tunnel creation, you must know which IPsec configurations have been created. This ensures that you choose the correct configurations when you enable an IPsec tunnel. Fabric OS 6.2 administrator guide 461