HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 158
LDAP in FIPS mode
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 158 highlights
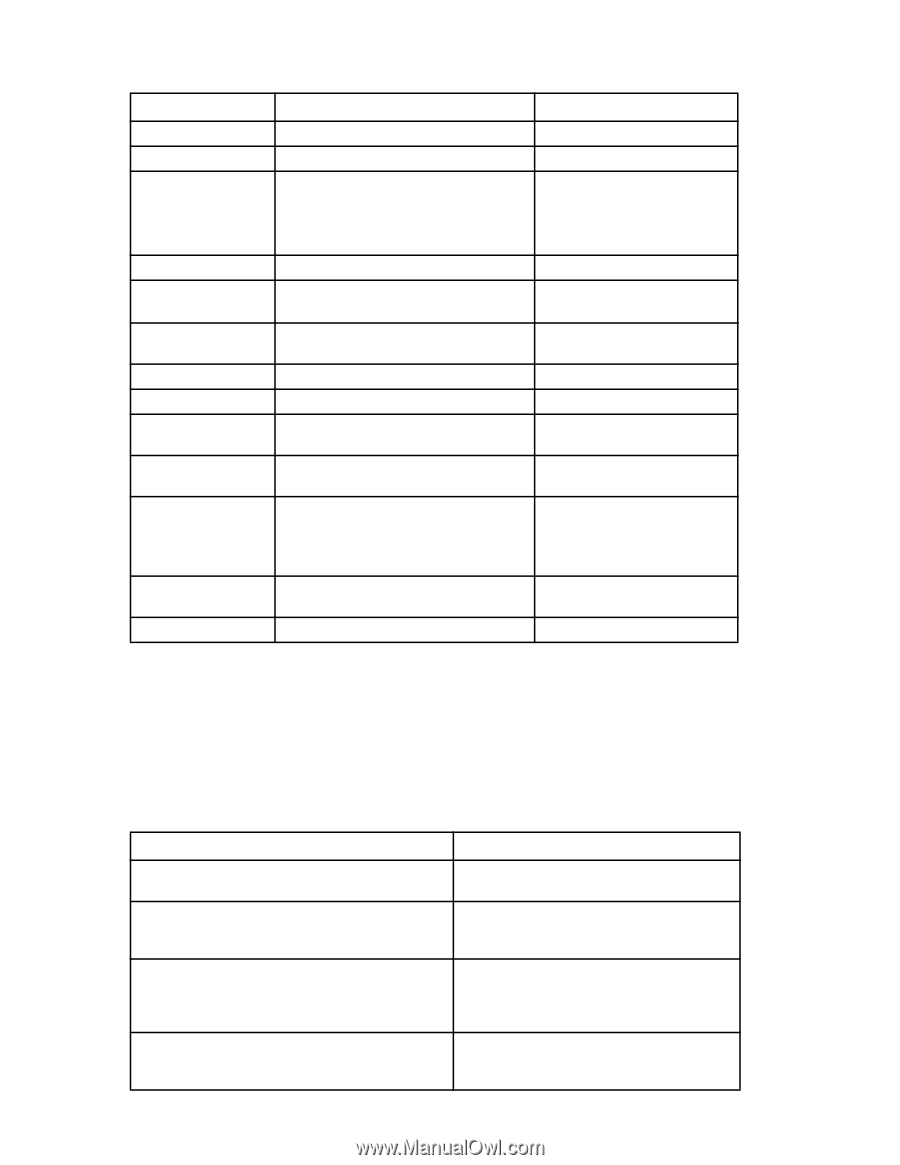
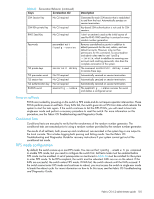
Only FIPS-compliant algorithms are run at this stage. Table 43 FIPS mode restrictions Features FIPS mode Non-FIPS mode Root account Telnet/SSH access SSH algorithms Disabled Only SSH • HMAC-SHA1 (mac) • 3DES-CBC, AES128-CBC, AES192-CBC, AES256-CBC (cipher suites) Enabled Telnet and SSH No restrictions HTTP/HTTPS access HTTPS protocol/algorithms HTTPS only TLS/AES128 cipher suite HTTP and HTTPS TLS/AES128 cipher suite (SSL will no longer be supported) RPC/secure RPC access Secure RPC protocols Secure RPC only TLS (AES128 cipher suite) RPC and secure RPC SSL and TLS (all cipher suites) SNMP DH-CHAP/FCAP hashing algorithms Read-only operations SHA-1 Read and write operations MD5 and SHA-1 Signed firmware Mandatory firmware signature validation. Configupload/ download/supports ave/ firmwaredownload SCP only Optional firmware signature validation FTP and SCP IPsec Radius auth protocols Usage of AES-XCBC, MD5, and DH group 0 and 1 is blocked. PEAP-MSCHAPv2 No restrictions CHAP, PAP, PEAP-MSCHAPv2 LDAP in FIPS mode You can configure your Microsoft Active Directory server to use LDAP while in FIPS mode. There is no option provided on the switch to configure TLS ciphers for LDAP in FIPS mode. However, the LDAP client checks whether FIPS mode is set on the switch and uses the FIPS-compliant TLS ciphers for LDAP. If the FIPS mode is not set and the Microsoft Active Directory server is configured for FIPS ciphers, it uses FIPS-compliant ciphers. Table 44 lists the differences between FIPS and non-FIPS modes of operation. Table 44 FIPS and non-FIPS modes of operation FIPS mode non-FIPS mode The CA who issued the Microsoft Active Directory server certificate must be installed on the switch. Configure FIPS compliant TLS ciphers [TDES-168, SHA1 and RSA-1024] on Microsoft Active Directory server. The host needs a reboot for the changes to take effect. There is no mandatory CA certificate installation on the switch. On the Microsoft Active Directory server, there is no configuration of the FIPS compliant TLS ciphers. The switch uses FIPS-compliant ciphers regardless of Microsoft Active Directory server configuration. If the Microsoft Active Directory server is not configured for FIPS ciphers, authentication will still succeed. The Microsoft Active Directory server certificate is validated by the LDAP client. If the CA certificate is not present on the switch, user authentication will fail. The Microsoft Active Directory server certificate is validated if the CA certificate is found on the switch If Microsoft Active Directory server is configured for FIPS ciphers and the switch is in non-FIPS mode, user authentication will succeed. 156 Configuring advanced security features