HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 160
LDAP certificates for FIPS mode
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 160 highlights
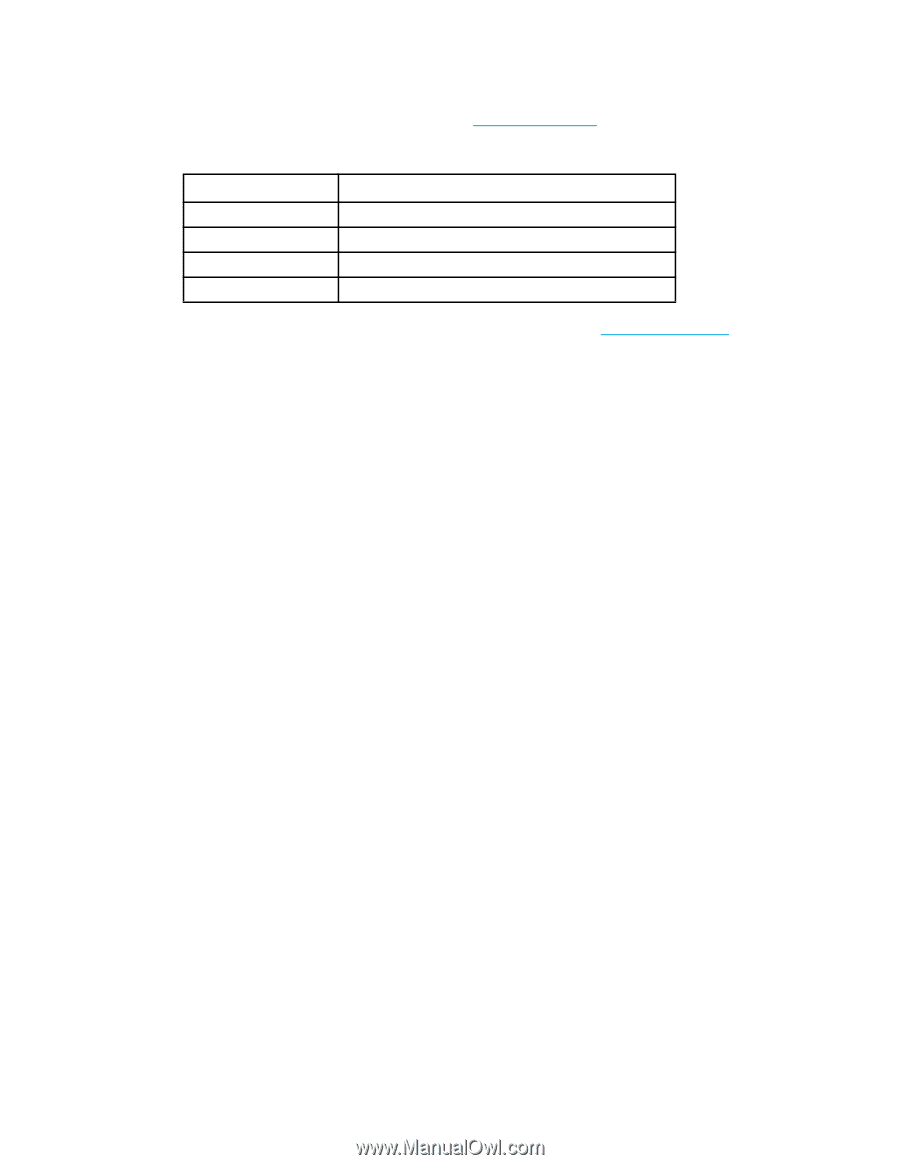
For additional Microsoft Active Directory settings: a. Set the following SCHANNEL settings listed in Table 45 to allow. To support FIPS compliant TLS cipher suites on Microsoft's Active Directory server, allow the SCHANNEL settings listed in Table 45. See www.microsoft.com for instructions on how to allow the SCHANNEL settings for the ciphers, hashes, key exchange, and the TLS protocol. Table 45 Active Directory Keys to modify Key Sub-key Ciphers Hashes Key exchange algorithm Protocols 3DES SHA1 PKCS TLSv1.0 b. Enable FIPS algorithm policy on the Microsoft Active Directory. See www.microsoft.com for instructions. LDAP certificates for FIPS mode To utilize the LDAP services for FIPS between the switch and the host, you must generate a CSR on the Active Directory server and import and export the CA certificates. To support server certificate validation, it is essential to have the CA certificate installed on the switch and Active Directory server. Use the secCertUtil to import the CA certificate to the switch. This will prompt for the remote IP and login credentials to retrieve the CA certificate. The CA certificate should be in any of the standard certificate formats, .cer, .crt, or .pem. For storing and obtaining CA certificates, follow the instructions earlier in this section. LDAP CA certificate file names should not contain spaces when using the secCertUtil command to import and export the certificate. Importing an LDAP switch certificate This option imports the LDAP CA certificate from the remote host to the switch. 1. Connect to the switch and log in as admin. 2. Enter the secCertUtil import -ldapcacert command. Example of importing an LDAP certificate switch:admin> seccertutil import -ldapcacert Select protocol [ftp or scp]: scp Enter IP address: 192.168.38.206 Enter remote directory: /users/aUser/certs Enter certificate name (must have ".crt" or ".cer" ".pem" suffix): LDAPTestCa.cer Enter Login Name: aUser Password: Success: imported certificate [LDAPTestCa.cer]. Exporting an LDAP switch certificate This option exports the LDAP CA certificate from the switch to the remote host. 1. Connect to the switch and log in as admin. 2. Enter the secCertUtil export -ldapcacert command. 158 Configuring advanced security features