HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2 administrator guide (5697-0 - Page 464
IPSec implementation over FCIP
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 464 highlights
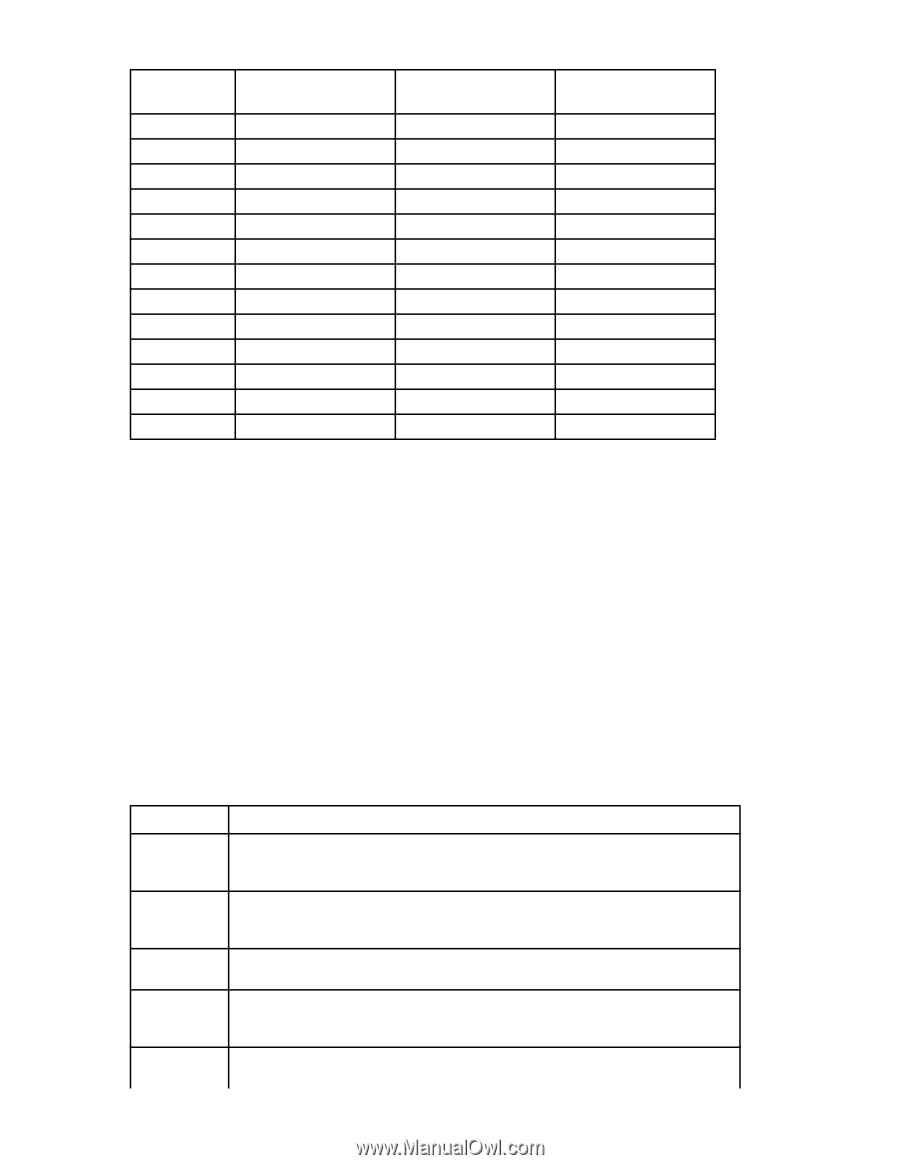
Table 91 Default Mapping of DSCP priorities to L2Cos Priorities (continued) Virtual CIrcuit (VC) DSCP priority/bits L2CoS priority/bits Assigned to: 3 15 / 001111 3 / 011 Medium QoS 4 19 / 010011 3 / 011 Medium QoS 5 23 / 010111 3 / 011 6 27 / 011011 0 / 000 7 31 / 011111 0 / 000 8 35 / 100011 0 / 000 Medium QoS Class 3 Multicast Broadcast/Multicast Low Qos 9 39 / 100111 0 / 000 Low Qos 10 43 / 101011 4 / 100 11 47 / 101111 4 / 100 12 51 / 110011 4 / 100 13 55 / 110111 4 / 100 High QoS High QoS High QoS High QoS 14 59 / 111011 15 63 / 111111 4 / 100 0 / 000 High QoS - IPSec implementation over FCIP Internet Protocol security (IPsec) uses cryptographic security to ensure private, secure communications over Internet Protocol networks. IPsec supports network-level data integrity, data confidentiality, data origin authentication, and replay protection. It helps secure your SAN against network-based attacks from untrusted computers, attacks that can result in the denial-of-service of applications, services, or the network, data corruption, and data and user credential theft. By default, when creating an FCIP tunnel, IPsec is disabled. Used to provide greater security in tunneling on a B-Series Multi-Protocol Router Blade or an HP StorageWorks 400 Multi-Protocol Router, the IPsec feature does not require you to configure separate security for each application that uses TCP/IP. When configuring for IPsec, however, you must ensure that there is a B-Series Multi-Protocol Router Blade or an HP StorageWorks 400 Multi-Protocol Router at each end of the FCIP tunnel. IPsec works on FCIP tunnels with or without IP compression (IPComp), FCIP Fastwrite, and Tape Pipelining. IPsec can be created only on tunnels using IPv4 addressing. IPsec requires the High-Performance Extension over FCIP/FC license. IPsec uses some terms that you should be familiar with before beginning your configuration. These are standard terms, but are included here for your convenience. Table 92 IPsec terminology Term Definition AES AES-XCBC AH DES 3DES Advanced Encryption Standard. FIPS 197 endorses the Rijndael encryption algorithm as the approved AES for use by US Government organizations and others to protect sensitive information. It replaces DES as the encryption standard. Cipher Block Chaining. A key-dependent one-way hash function (MAC) used with AES in conjunction with the Cipher-Block-Chaining mode of operation, suitable for securing messages of varying lengths, such as IP datagrams. Authentication Header - like ESP, AH provides data integrity, data source authentication, and protection against replay attacks but does not provide confidentiality. Data Encryption Standard is the older encryption algorithm that uses a 56-bit key to encrypt blocks of 64-bit plain text. Because of the relatively shorter key length, it is not a secured algorithm and no longer approved for Federal use. Triple DES is a more secure variant of DES. It uses three different 56-bit keys to encrypt blocks of 64-bit plain text. The algorithm is FIPS-approved for use by Federal agencies. 460 Configuring and monitoring FCIP extension services