VMware VLM3-ENG-CP User Guide - Page 172
Why Should I Fence Configurations?, How Does Fencing Work?
 |
View all VMware VLM3-ENG-CP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 172 highlights
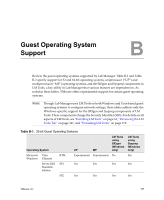
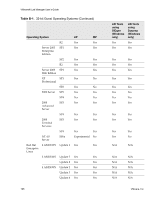
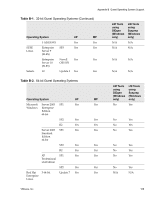
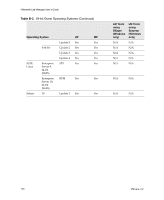
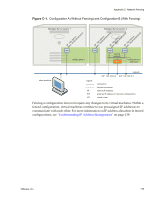
VMware® Lab Manager User's Guide Why Should I Fence Configurations? Typically, you want to enable network fencing under these circumstances: „ You have a configuration with one or more servers, and you anticipate cloning the configuration numerous times. „ You have a configuration involving a difficult and complex setup, and cloning the configuration is an easier route than repeating the setup. With fencing, engineers can run multiple, independent tests on a configuration deployed multiple times. Fencing is particularly useful when a developer needs to examine a bug without interrupting or stopping ongoing testing on a configuration. Lab Manager also enables you to reproduce the bug at a later time if the developer is unavailable. The default number of concurrently deployed fenced configurations on a Managed Server system is 20. If you need more configurations, you can increase the number without any penalty. From a performance perspective, network fencing impacts the traffic flow between modules. Fencing requires a slightly higher number of resources on the Managed Server system, such as memory, CPU, networking, and virtual machine slots. If you enable fencing but never use it, these resources do not come into play. How Does Fencing Work? Virtual machines in a configuration have preconfigured (internal) IP addresses. When you deploy virtual machines in fenced mode, Lab Manager assigns a unique external IP address to each of these machines. Through these external addresses, virtual machines both inside and outside the fence can communicate with each other. Lab Manager uses a virtual router to route packets between these virtual machines. Lab Manager configures the virtual router when you deploy a fenced configuration and deletes it when you undeploy the configuration. Figure C‐1 illustrates configurations without fencing and with fencing. 172 VMware, Inc.