Intel 925 Data Sheet - Page 170
SMM Access through GTT TLB, Memory Shadowing, I/O Address Space
 |
UPC - 683728067724
View all Intel 925 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 170 highlights
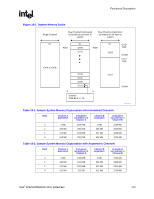
System Address Map R 9.4.7 9.4.8 9.4.9 SMM Access through GTT TLB Accesses through GTT TLB address translation to enabled SMM DRAM space are not allowed. Writes will be routed to memory address 0h with byte enables de-asserted and reads will be routed to memory address 0h. If a GTT TLB translated address hits enabled SMM DRAM space, an Invalid Translation Table Entry Flag is reported to BIOS. PCI Express and DMI originated accesses are never allowed to access SMM space directly or through the GTT TLB address translation. If a GTT TLB translated address hits enabled SMM DRAM space, an Invalid Translation Table Entry Flag is reported to BIOS. PCI Express and DMI write accesses through the graphics memory range set up by BIOS will be snooped. If, when translated, the resulting physical address is to enabled SMM DRAM space, the request will be remapped to address 0h with de-asserted byte enables. PCI Express and DMI read accesses to the graphics memory range set up by BIOS are not supported; therefore, users/systems will be remapped to address 0h. The read will complete with UR (unsupported request) completion status. GTT fetches are always decoded (at fetch time) to ensure they are not in SMM (actually, anything above base of TSEG or 640 KB-1 MB). Thus, they will be invalid and go to address 0h. This is not specific to PCI Express or DMI; it applies to the processor. Also, since the graphics memory range snoop would not be directly to SMM space, there would not be a writeback to SMM. In fact, the writeback would also be invalid (because it uses the same translation) and goes to address 0h. Memory Shadowing Any block of memory that can be designated as "read only" or "write only" can be "shadowed" into MCH main memory. Typically, this is done to allow ROM code to execute more rapidly out of main DRAM memory. ROM is used as read-only during the copy process while main DRAM memory at the same time is designated write-only. After copying, the main DRAM memory is designated read-only so that ROM is shadowed. Processor bus transactions are routed accordingly. I/O Address Space The MCH does not support the existence of any other I/O devices beside itself on the processor bus. The MCH generates either DMI or PCI Express bus cycles for all processor I/O accesses that it does not claim. Within the host bridge, the MCH contains two internal registers in the processor I/O space. These locations are used to implement a configuration space access mechanism. The processor allows 64 KB+3 bytes to be addressed within the I/O space. The MCH propagates the processor I/O address without any translation on to the destination bus; therefore, providing addressability for 64 KB+3 byte locations. Note that the upper 3 locations can be accessed only during I/O address wrap-around when processor bus HA16# address signal is asserted. HA16# is asserted on the processor bus when an I/O access is made to 4 bytes from address 0FFFDh, 0FFFEh, or 0FFFFh. HA16# is also asserted when an I/O access is made to 2 bytes from address 0FFFFh. 170 Intel® 82925X/82925XE MCH Datasheet