Cisco IPS-4255-K9 Installation Guide - Page 28
Interface Restrictions, Designating the Alternate TCP Reset Interface
 |
UPC - 746320951096
View all Cisco IPS-4255-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
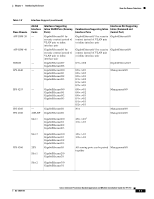
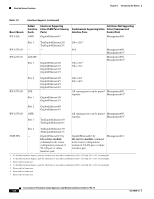
How the Sensor Functions Chapter 1 Introducing the Sensor Table 1-3 Alternate TCP Reset Interfaces (continued) Sensor Alternate TCP Reset Interface IPS 4260 Any sensing interface IPS 4270-20 Any sensing interface NME IPS None 1. This is an internal interface on the Catalyst backplane. Designating the Alternate TCP Reset Interface You need to designate an alternate TCP reset interface in the following situations: • When a switch is being monitored with either SPAN or VACL capture and the switch does not accept incoming packets on the SPAN or VACL capture port. • When a switch is being monitored with either SPAN or VACL capture for multiple VLANs, and the switch does not accept incoming packets with 802.1q headers. Note The TCP resets need 802.1q headers to tell which VLAN the resets should be sent on. • When a network tap is used for monitoring a connection. Note Taps do not permit incoming traffic from the sensor. You can only assign a sensing interface as an alternate TCP reset interface. You cannot configure the management interface as an alternate TCP reset interface. Interface Restrictions The following restrictions apply to configuring interfaces on the sensor: • Physical Interfaces - On modules (AIM IPS, AIP SSM, IDSM2, and NME IPS), all backplane interfaces have fixed speed, duplex, and state settings. These settings are protected in the default configuration on all backplane interfaces. - For nonbackplane FastEthernet interfaces the valid speed settings are 10 Mbps, 100 Mbps, and auto. Valid duplex settings are full, half, and auto. - For Gigabit copper interfaces (1000-TX on the IPS 4240, IPS 4255, IPS 4260, and IPS 4270-20), valid speed settings are 10 Mbps, 100 Mbps, 1000 Mbps, and auto. Valid duplex settings are full, half, and auto. - For Gigabit (copper or fiber) interfaces, if the speed is configured for 1000 Mbps, the only valid duplex setting is auto. - The command and control interface cannot also serve as a sensing interface. 1-10 Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0 OL-18504-01