Cisco IPS-4255-K9 Installation Guide - Page 42
Introducing the IDSM2
 |
UPC - 746320951096
View all Cisco IPS-4255-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
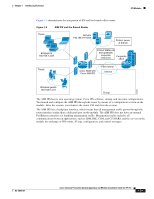
IPS Modules Chapter 1 Introducing the Sensor Figure 1-8 DMZ Configuration HTTP client ASA security appliance 10.10.10.10 Inside 10.10.10.0 Outside 209.165.200.225 DMZ 10.30.30.0 Internet HTTP client HTTP client 148403 Web server 10.30.30.30 In Figure 1-8 an HTTP client (10.10.10.10) on the inside network initiates HTTP communications with the DMZ web server (30.30.30.30). HTTP access to the DMZ web server is provided for all clients on the Internet; all other communications are denied. The network is configured to use an IP pool (a range of IP addresses available to the DMZ interface) of addresses between 30.30.30.50 and 30.30.30.60. For More Information • For more information on setting up ASA, refer to the Getting Started Guides found at this URL: http://www.cisco.com/en/US/products/ps6120/prod_installation_guides_list.html • For more information on installing the AIP SSM, see Installing the AIP SSM, page 6-3. • For more information on configuring the AIP SSM to receive IPS traffic, refer to Configuring the AIP SSM. Introducing the IDSM2 The Cisco Catalyst 6500 Series Intrusion Detection System Services Module (IDSM2) is a switching module that performs intrusion prevention in the Catalyst 6500 series switch and 7600 series router. You can use the CLI or IDSM to configure the IDSM2. You can configure the IDSM2 for promiscuous or inline mode. The IDSM2 performs network sensing-real-time monitoring of network packets through packet capture and analysis. The IDSM2 captures network packets and then reassembles and compares the packet data against attack signatures indicating typical intrusion activity. Network traffic is either copied to the IDSM2 based on security VACLs in the switch or is copied to the IDSM2 through the SPAN port feature of the switch. These methods route user-specified traffic to the IDSM2 based on switch ports, VLANs, or traffic type to be inspected (Figure 1-9 on page 1-25). 1-24 Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0 OL-18504-01