Cisco IPS-4255-K9 Installation Guide - Page 37
Appliance Restrictions, Connecting an Appliance to a Terminal Server - parts
 |
UPC - 746320951096
View all Cisco IPS-4255-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 37 highlights
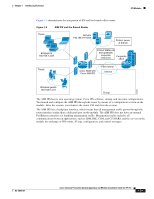
Chapter 1 Introducing the Sensor IPS Appliances After being installed at key points in the network, the appliance monitors and performs real-time analysis of network traffic by looking for anomalies and misuse based on an extensive, embedded signature library. When the system detects unauthorized activity, appliances can terminate the specific connection, permanently block the attacking host, log the incident, and send an alert to the manager. Other legitimate connections continue to operate independently without interruption. Appliances are optimized for specific data rates and are packaged in Ethernet, Fast Ethernet, and Gigabit Ethernet configurations. In switched environments, appliances must be connected to the SPAN port or VACL capture port of the switch. The Cisco IPS 4200 series appliances provide the following: • Protection of multiple network subnets through the use of up to eight interfaces • Simultaneous, dual operation in both promiscuous and inline modes • A wide array of performance options-from 80 Mbps to multiple gigabits • Embedded web-based management solutions packaged with the sensor For More Information • For a list of IPS documents and how to access them, refer to Documentation Roadmap for Cisco Intrusion Prevention System 7.0. • For a list of supported appliances, see Supported Sensors, page 1-17. • For a description of each IPS appliance, see the following chapters in this document: - Chapter 2, "Installing the IPS 4240 and the IPS 4255" - Chapter 3, "Installing the IPS 4260" - Chapter 4, "Installing the IPS 4270-20" Appliance Restrictions The following restrictions apply to using and operating the appliance: • The appliance is not a general purpose workstation. • Cisco Systems prohibits using the appliance for anything other than operating Cisco IPS. • Cisco Systems prohibits modifying or installing any hardware or software in the appliance that is not part of the normal operation of the Cisco IPS. Connecting an Appliance to a Terminal Server A terminal server is a router with multiple, low speed, asynchronous ports that are connected to other serial devices. You can use terminal servers to remotely manage network equipment, including appliances. To set up a Cisco terminal server with RJ-45 or hydra cable assembly connections, follow these steps: Step 1 Connect to a terminal server using one of the following methods: • For terminal servers with RJ-45 connections, connect a 180 rollover cable from the console port on the appliance to a port on the terminal server. • For hydra cable assemblies, connect a straight-through patch cable from the console port on the appliance to a port on the terminal server. OL-18504-01 Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0 1-19