Cisco IPS-4255-K9 Installation Guide - Page 43
Introducing the NME IPS
 |
UPC - 746320951096
View all Cisco IPS-4255-K9 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 43 highlights
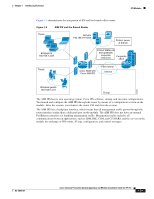
Chapter 1 Introducing the Sensor IPS Modules Figure 1-9 IDSM2 Block Diagram Source traffic Destination traffic Cisco 6500 switch Switch backplane Copied VACL traffic or SPAN traffic to IDSM-2 monitor port Destination traffic Source traffic IDSM-2 Alarms and configuration through IDSM-2 command and control port 148404 IPS management console The IDSM2 searches for patterns of misuse by examining either the data portion and/or the header portion of network packets. Content-based attacks contain potentially malicious data in the packet payload, whereas, context-based attacks contain potentially malicious data in the packet headers. You can configure the IDSM2 to generate an alert when it detects potential attacks. Additionally, you can configure the IDSM2 to transmit TCP resets on the source VLAN, generate an IP log, and/or initiate blocking countermeasures on a firewall or other managed device. Alerts are generated by the IDSM2 through the Catalyst 6500 series switch backplane to the IPS manager, where they are logged or displayed on a graphical user interface. For More Information • For more information on installing the IDSM2, see Installing the IDSM2, page 7-5. • For more information on configuring the IDSM2 to receive IPS traffic, refer to Configuring the IDSM2. Introducing the NME IPS Cisco Intrusion Prevention System Network Module (NME IPS) integrates and brings inline Cisco IPS functionality to Cisco access routers. You can install the NME IPS in any one of the network module slots in the 2800 and 3800 series router. The NME IPS has its own operating system, Cisco IPS software, startup, and run-time configurations. You launch and configure the modules through the router by means of a configuration session on the modules. After the session, you return to the router CLI and clear the session. For the NME IPS, all management traffic passes through the external FastEthernet interface on the module. Management traffic includes all communications between applications, such as IDM, IME, CSM, and CS-MARS, and the servers on the module for exchange of IPS events, IP logs, configuration, and control messages. OL-18504-01 Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.0 1-25