VMware 4817V62 Administration Guide - Page 216
Hierarchical Inheritance of Permissions
 |
View all VMware 4817V62 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 216 highlights
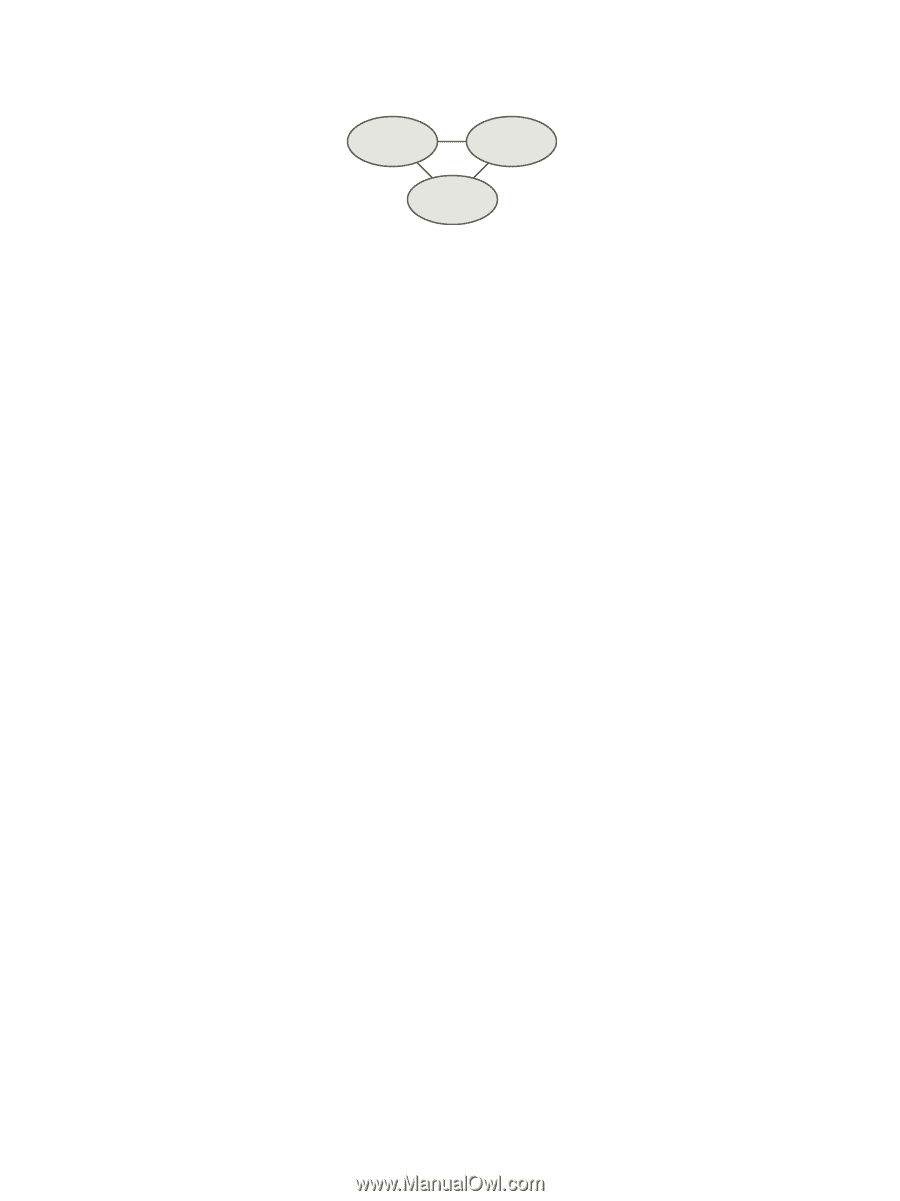
vSphere Basic System Administration Figure 18-1. The Conceptual Structure of a Permission permission = role user or group object By default, all users who are members of the Windows Administrators group on the vCenter Server system have the same access rights as any user assigned to the Administrator role on all objects. When connecting directly to an ESX/ESXi host, the root and vpxuser user accounts have the same access rights as any user assigned the Administrator role on all objects. All other users initially have no permissions on any objects, which means they cannot view these objects or perform operations on them. A user with Administrator privileges must assign permissions to these users to allow them to perform necessary tasks. Many tasks require permissions on more than one object. Some general rules can help you determine where you must assign permissions to allow particular operations: n Any operation that consumes storage space, such as creating a virtual disk or taking a snapshot, requires the Datastore.Allocate Space privilege on the target datastore, as well as the privilege to perform the operation itself. n Moving an object in the inventory hierarchy requires appropriate privileges on the object itself, the source parent object (such as a folder or cluster), and the destination parent object. n Each host and cluster has its own implicit resource pool that contains all the resources of that host or cluster. Deploying a virtual machine directly to a host or cluster requires the Resource.Assign Virtual Machine to Resource Pool privilege. Hierarchical Inheritance of Permissions When you assign a permission to an object, you can choose whether the permission propagates down the object hierarchy. Propagation is set per permission, not universally applied. Permissions defined for a child object always override those propagated from parent objects. Figure 18-2 illustrates the vSphere inventory hierarchy, and the paths by which permissions can propagate. 216 VMware, Inc.