VMware 4817V62 Administration Guide - Page 219
Example 2: Child Permissions Overriding Parent Permissions,
 |
View all VMware 4817V62 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 219 highlights
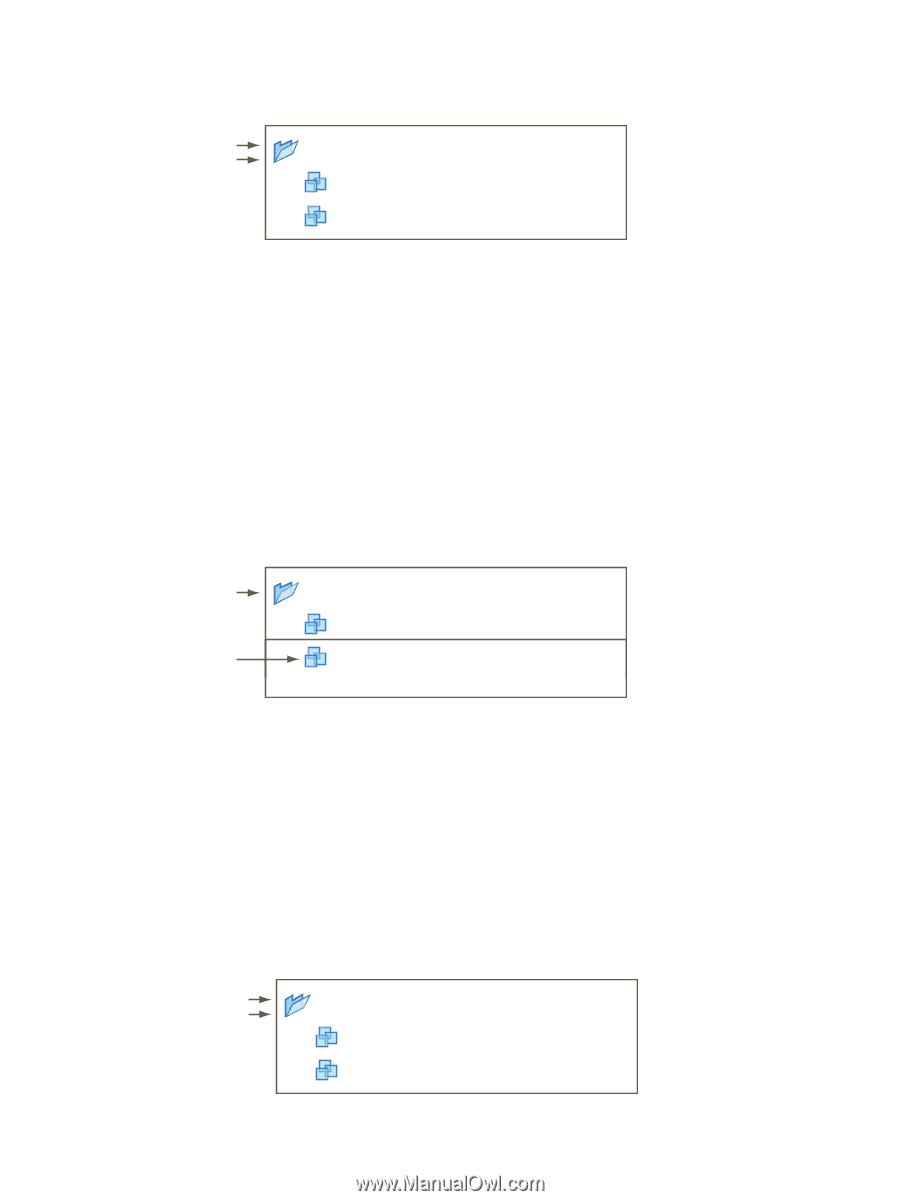
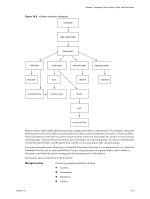
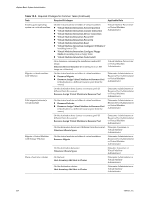
Chapter 18 Managing Users, Groups, Roles, and Permissions Figure 18-3. Example 1: Inheritance of Multiple Permissions group A + role 1 group B + role 2 VM Folder VM A VM B user 1 has permissions of role 1 and role 2 Example 2: Child Permissions Overriding Parent Permissions This example illustrates how permissions assigned on a child object override permissions assigned on a parent object. You can use this overriding behavior to restrict user access to particular areas of the inventory. In this example, permissions are to two different groups on two different objects. n Role 1 can power on virtual machines. n Role 2 can take snapshots of virtual machines. n Group A is granted Role 1 on VM Folder, with the permission set to propagate to child objects. n Group B is granted Role 2 on VM B. User 1, who belongs to groups A and B, logs on. Because Role 2 has been assigned at a lower point in the hierarchy than Role 1, it overrides Role 1 on VM B. User 1 can power on VM A, but not take snapshots. User 1 can take snapshots of VM B, but not power it on. Figure 18-4. Example 2: Child Permissions Overriding Parent Permissions group A + role 1 group B + role 2 VM Folder VM A VM B user 1 has permissions of role 1 only user 1 has permissions of role 2 only Example 3: User Permissions Overriding Group Permissions This example illustrates how permissions assigned directly to an individual user override permissions assigned to a group that the user is a member of. In this example, permissions are assigned to a user and to a group on the same object. n Role 1 can power on virtual machines. n Group A is granted Role 1 on VM Folder. n User 1 is granted No Access role on VM Folder. User 1, who belongs to group A, logs on. The No Access role granted to User 1 on VM Folder overrides the group permission. User 1 has no access to VM Folder or VMs A and B. Figure 18-5. Example 3: User Permissions Overriding Group Permissions group A + role 1 user 1 + no access VM Folder VM A VM B user 1 has no access to the folder or the virtual machines VMware, Inc. 219